Secure Video Sharing: Best Practices for Corporate Video Sharing
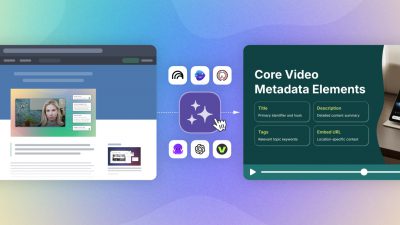
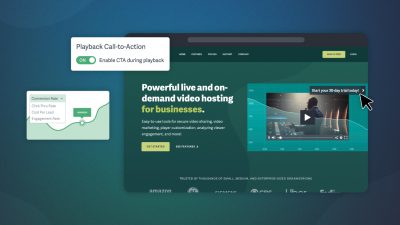
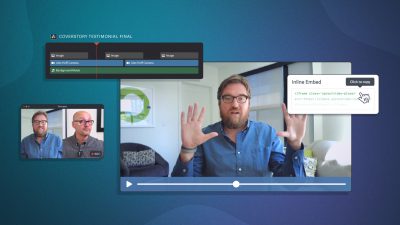
6 MIN TO READ Don’t bet on luck: collaborate seamlessly with secure video sharing. Control exactly who watches, when, and where. Protect videos from downloads and leaks, control who gets access, and see who’s watching. Discover six simple steps for secure business video sharing.