Video drives business communication and collaboration. But how do you protect sensitive or confidential footage from downloads, breaches, and theft?
Enter secure video sharing: control exactly who watches, when, and where.
Businesses distribute confidential videos with peace of mind by using a secure video hosting platform. Keep your videos safe while collaborating efficiently with secure sharing features, like password protection, viewer logins, single sign-on (SSO), and dynamic watermarks.
In this guide, you’ll learn six simple steps to share videos securely and build a smarter, safer system for internal communication.
The Importance of Secure Business Video Sharing
Internal video sharing keeps teams aligned and informed. But what’s at stake when your internal videos are shared without permission?
When videos contain sensitive information, such as product demos, trade secrets, or confidential material, protect every file with secure video sharing.
Think of it this way: an unauthorized view could compromise your next big product launch, wasting money and forcing marketing to pivot last minute. Or worse, financial data leaks, hurting your brand and exposing the company to legal liability.
These are extreme examples. But they illustrate the importance of securely sharing video to protect your business as a whole.
How to Share Video Securely: The Three Pillars
Consider all access points and opportunities for leaks to keep videos safe. To do this, build your secure video sharing strategy around three pillars:
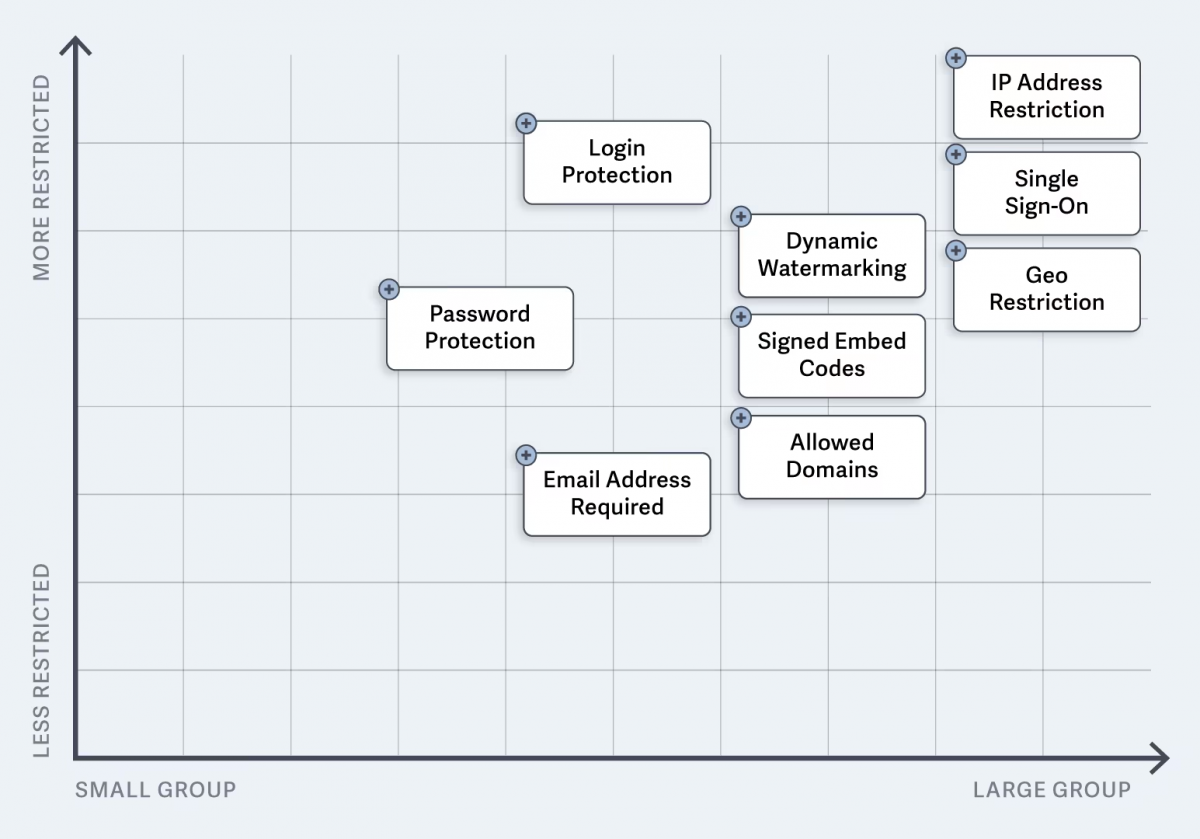
- Control Video Access: Limit who can watch your videos and safeguard your account. This includes passwords, logins, location restrictions, and single sign-on.
- Prevent Leaks and Theft: Stop unauthorized distribution and deter screen recording. This includes allowed domains, signed embed codes, and dynamic watermarks.
- Audit Your Security: Regularly monitor engagement data and viewer logs. With SproutVideo, review engagement metrics, your account audit log, and viewer access log.
For example, a company embeds a video for new employees on its internal website. New hires access the video by entering their login credentials. As they watch, a visible dynamic watermark moves around the screen, displaying their personal information. Additionally, the video is restricted to their IP address; therefore, they can only play the video on this specific internet network.
This stack of security measures ensures the viewer must have viewer access to watch, the watermark deters recording by revealing the viewer’s information on-screen, and only whitelisted networks of computers can play the video.
Ready to get started? Try every feature of the SproutVideo platform free for 30 days.
6 Steps to Secure Video Content for Business
1. Determine the Level of Security You Require
Use the following questions to determine the types of security and privacy features your business needs.
- How sensitive is the video content? How would your business be impacted if these videos leaked?
- Do you already have a website where you can embed these videos, or do you need a secure portal for your videos as well?
- Should viewers be able to access your videos seamlessly? Should videos be password-protected or require viewer logins?
- Where can viewers access the video? Do viewers need access on the go, or should access be restricted to specific locations, such as the office?
- Who should have access to these videos at your company? Should videos be restricted to specific teams or locations?
The answers to these questions will largely determine the features you need to look for when seeking a secure video hosting platform.
2. Choose Your Secure Video Hosting Platform
Secure online video hosting platforms are not one-size-fits-all solutions.
Considering the questions you answered above, determine the secure video sharing features that are essential to your business.
Popular free options, such as YouTube and TikTok, are ideal for social media marketing. However, secure video hosting platforms for business put control and privacy at the center of their product.
Secure Video Hosting Platform: What Features Do You Need?
- Password-Protected Video: Require a password to access video content.
- Secure Video Login: Create login credentials that are required to view videos.
- Signed Embed Codes: Prevent embed code theft. Once expired, the video can no longer be played where embedded.
- Whitelist Access to Content: Control what IP addresses, domains, and geographic locations have access to your content.
- Single Sign-On (SSO): User authentication with one set of credentials. Connect your hosted video website (such as SproutVideo) with your Identity Provider.
- Dynamic Watermarking: Display the viewer’s email address, IP address, and session ID on the video to deter theft.
- Block Search Engine Indexing: Block indexing to prevent your public content from appearing in search results.
- Account Audit Log: Review team members’ changes to videos and privacy settings.
- Viewer Access Log: Track individual viewer engagement and view who accessed your videos, along with the time spent watching.
Review the essential features of a secure video platform above, and make a list of the solutions your business requires. All of the features above are found on the SproutVideo platform.
Learn More: 7 Reasons Businesses Use Private Video Hosting Platforms vs YouTube
3. Restrict Video Access
To limit who can view videos, you have two options. You can restrict viewer access:
- To the video with credentials
- By geographic location or IP network
You can also combine these restrictions for layered security.
Restrict Viewer Access to the Video
First, consider where you share videos. Are you securely sharing video on:
- Your website (including an intranet, SharePoint, Squarespace, WordPress, etc.)
- Your video portal via a video hosting platform, like SproutVideo.
- A third-party platform, such as Notion, Confluence, or Asana.
To create a seamless viewing experience, ensure that viewers can access the webpage where your videos are located, rather than needing to enter credentials for each video individually.
For example, if you share videos on an internal company website that already includes page access controls, use these controls to manage employees’ access credentials or profiles.
For more granular access permissions, you can also combine additional restriction features such as login protection or password protection. You can also bring your Identity Provider and use single sign-on (SSO) with our hosted video websites.
Need a secure video website? Create a dedicated video portal in minutes.
Restrict Access by Location or Network
Ensure no one outside your organization can access content, even with valid credentials.
To do this, use IP address and geographic location restrictions.
For example, a company whitelists its computer network and the IP addresses of any remote employees. Computers outside those networks are blocked from loading videos or live streams.
4. Deter Screen Recording & Prevent Downloads
Once a viewer has access to video content, how do you ensure its protection?
- Prevent Downloads
- Dynamic Watermarks
Let’s discuss.
Prevent Downloads
A secure video hosting platform, such as SproutVideo, prevents videos from being downloaded by default; however, video embed codes are essential, as opposed to using links.
Dynamic Watermarks
Deter screen recording and track unauthorized copies with dynamic watermarking.
Watermarking varies by video hosting platform. On the SproutVideo platform, you can enable visible or invisible watermarks (or both).
- Visible Watermarks: A burned-in watermark that displays the viewer’s email address, IP address, and session ID. It is designed to be difficult to remove and changes positions, making it hard for content thieves to blur or crop out their personal information.
- Invisible Watermarks: Invisible to viewers, our team can detect the invisible mark and use it to identify the source of any unauthorized copies of your content.
You can also customize the appearance of visible dynamic watermarks: change the opacity, interval timing, and prevent the watermark from covering center-focused content.
Learn More: Dynamic Watermarks for Videos
5. Safeguard Embed Codes
Unless preventative measures are in place, it is relatively easy to locate a video embed code on a webpage to copy and paste it on another site. There are two major ways to prevent this:
- Domain restriction automatically checks the URL where your embed code is located to ensure it’s approved. The video won’t load unless it has been approved.
- Signed embed codes require a unique signing key to play the video. The video won’t load if the signing key is absent or incorrect.
While more technically advanced, signed embed codes can be used in more complex scenarios than allowed domains.
6. Track Viewer Activity
Periodically review who has been accessing your videos:
- Engagement Metrics: Check data for unusual email addresses, locations, IP addresses, or viewing patterns. If anything stands out, consider temporarily revoking viewer access, adjusting the privacy settings, or removing it from the page.
- Viewer Access Log: Track viewer engagement by the individual; view who accessed your videos and the time spent watching.
- Account Audit Log: Track team member activity. Easily check and see who uploaded a video, changed a privacy setting, or edited a detail about your account.
How to Track Individual Viewers
Easily identify viewers by tagging them (on the SproutVideo platform). You can skip this step when using login protection or single sign-on (SSO), as viewers are automatically tracked.
Secure Video Hosting: Platform Overview
See these features in action with our platform walkthrough video below. Ready to get started? Visit our companion help guide to get started.